Obfuscating Your Plugins with ProGuard
The plugin obfuscation has been officially described in great detail, see: obfuscate the plugin
So without further ado, this post will be a step-by-step demonstration of obfuscating your plugin with ProGuard, starting with a real-world example.
To see the comparison file, the key code of ProGuard obfuscation is added to this commit, all the code for this post in this repository
Added ProGuard
Section titled “Added ProGuard”In build.gradle.kts, add the buildscript node to import the proguard dependency
buildscript { repositories { maven { setUrl("https://maven.aliyun.com/repository/public/") setUrl("https://maven.aliyun.com/nexus/content/groups/public/") setUrl("https://plugins.gradle.org/m2/") setUrl("https://oss.sonatype.org/content/repositories/snapshots/") } mavenCentral() gradlePluginPortal() }
dependencies { classpath("com.guardsquare:proguard-gradle:7.3.2") }}Configuring ProGuard
Section titled “Configuring ProGuard”Register a new task in build.gradle.kts:
// Register a new task, task name is "proguard" register<proguard.gradle.ProGuardTask>("proguard") { dependsOn(instrumentedJar) verbose()
val javaHome = System.getProperty("java.home") File("$javaHome/jmods/").listFiles()!!.forEach { libraryjars(it.absolutePath)}
// Use the jar task output as a input jar. This will automatically add the necessary task dependency. injars("build/libs/instrumented-${properties("pluginName")}-${properties("pluginVersion")}.jar") outjars("build/obfuscated/output/instrumented-${properties("pluginName")}-${properties("pluginVersion")}.jar")
libraryjars(configurations.compileClasspath.get())
dontshrink() dontoptimize()
adaptclassstrings("**.xml") adaptresourcefilecontents("**.xml")
// Allow methods with the same signature, except for the return type, // to get the same obfuscation name. overloadaggressively()
// Put all obfuscated classes into the nameless root package. repackageclasses("") dontwarn()
printmapping("build/obfuscated/output/${properties("pluginName")}-${properties("pluginVersion")}-ProGuard-ChangeLog.txt")
target(properties("pluginVersion"))
adaptresourcefilenames() optimizationpasses(9) allowaccessmodification()
keepattributes("Exceptions,InnerClasses,Signature,Deprecated,SourceFile,LineNumberTable,*Annotation*,EnclosingMethod")
keep(""" class * implements com.intellij.openapi.components.PersistentStateComponent {*;} """.trimIndent() )
keepclassmembers(""" class * {public static ** INSTANCE;} """.trimIndent() ) keep("class com.intellij.util.* {*;}") }
prepareSandbox { if (properties("enableProGuard").toBoolean()) { dependsOn("proguard") pluginJar.set(File("build/obfuscated/output/instrumented-${properties("pluginName")}-${properties("pluginVersion")}.jar")) } }These are the syntax of ProGuard, for more rules see: Official ProGuard Documentation, we focus on the last keep and keepclassmembers.
Build test
Section titled “Build test”After the configuration is complete, run the plugin and the debug message is as follows:
21:40:12: Executing 'runIde'...
Starting Gradle Daemon...Connected to the target VM, address: '127.0.0.1:12563', transport: 'socket'Gradle Daemon started in 915 ms> Task :initializeIntelliJPlugin> Task :patchPluginXml UP-TO-DATE
> Task :verifyPluginConfiguration[gradle-intellij-plugin :verifyPluginConfiguration] The following plugin configuration issues were found:- The Java configuration specifies sourceCompatibility=11 but IntelliJ Platform 2022.3.3 requires sourceCompatibility=17.See: https://jb.gg/intellij-platform-versions
> Task :compileKotlin NO-SOURCE> Task :compileJava UP-TO-DATE> Task :processResources UP-TO-DATE> Task :classes UP-TO-DATE> Task :setupInstrumentCode> Task :instrumentCode UP-TO-DATE> Task :jar UP-TO-DATE> Task :inspectClassesForKotlinIC UP-TO-DATE> Task :instrumentedJar UP-TO-DATE> Task :proguard <=== proguard task 已经成功执行。> Task :prepareSandboxDisconnected from the target VM, address: '127.0.0.1:12563', transport: 'socket'Connected to the target VM, address: 'localhost:12616', transport: 'socket'Obfuscated results
Section titled “Obfuscated results”After obfuscated:
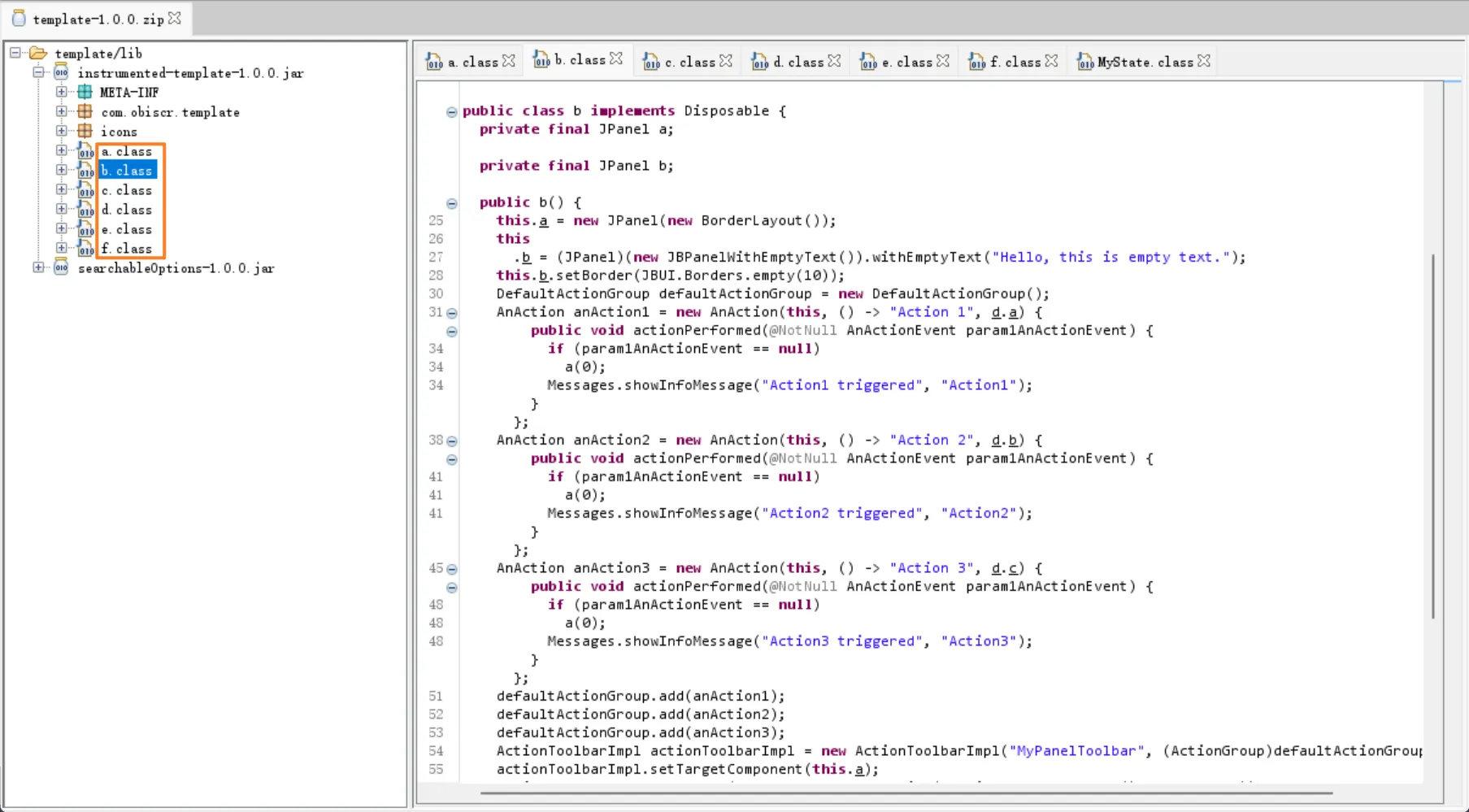
On the left side, file names have been obfuscated, and on the right side, file class names, method names, and variable names have been obfuscated.
This is just a very basic obfuscation effect, if you need more complex. You can refer to the ProGuard official documentation mentioned above.
Special circumstances
Section titled “Special circumstances”In IntelliJ plugin projects, there are some files that are not to be obfuscated. Two cases are listed in this demo.
Called via reflection
Section titled “Called via reflection”One of the files in the project is MyDefaultFileType.java. This file adds a new file type, let's call it a J-file, with a *.j or *.J file extension.
This file has already been registered in plugin.xml
<extensions defaultExtensionNs="com.intellij"> ... <fileType name="MyNativeFile" implementationClass="com.obiscr.template.MyDefaultFileType" fieldName="INSTANCE" extensions="j;J" order="first"/> ...</extensions>The key point here is a fieldName attribute: INSTANCE, which corresponds to INSTANCE in MyDefaultFileType.java. In other words, they have to be the same. Otherwise the property will not be found when the call is reflected off.
For example, once we've removed the proguard task's
register<proguard.gradle.ProGuardTask>("proguard") { ...
// keepclassmembers(""" // class * {public static ** INSTANCE;} // """.trimIndent() // ) ... }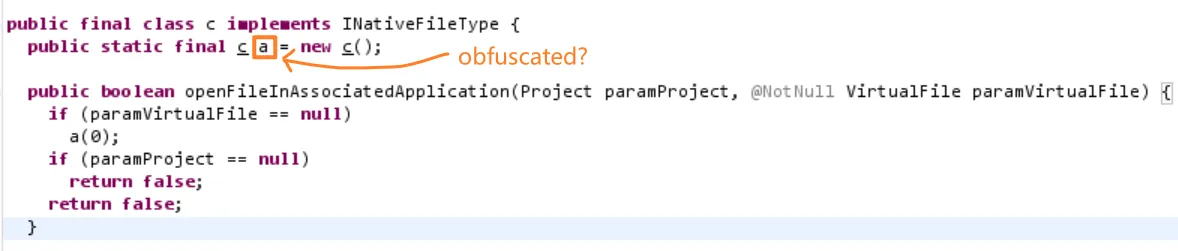
Run the plugin and you get an error:
2023-09-24 21:31:18,647 [ 3018] WARN - #c.i.e.RunManager - Must be not called before project components initializedInfo | RdCoroutineScope | 53:DefaultDispatcher-worker-35 | RdCoroutineHost overridden2023-09-24 21:31:21,580 [ 5951] SEVERE - #c.i.o.f.i.FileTypeManagerImpl - INSTANCEjava.lang.NoSuchFieldException: INSTANCE at java.base/java.lang.Class.getDeclaredField(Class.java:2610) at com.intellij.openapi.fileTypes.impl.FileTypeManagerImpl.instantiateFileTypeBean(FileTypeManagerImpl.java:492) at com.intellij.openapi.fileTypes.impl.FileTypeManagerImpl.mergeOrInstantiateFileTypeBean(FileTypeManagerImpl.java:463)It shows that the INSTANCE attribute could not be found. So for this case, you can use proguard's keepclassmembers to keep the INSTANCE attribute from being obfuscated in all classes. Of course, you can also keep INSTANCE from being obfuscated in all classes that implements INativeFileType if you want. This is a more precise control.
You may ask, since this problem can be avoided by keeping the fieldName in plugin.xml the same as INSTANCE in MyDefaultFileType.java, wouldn't it be possible to avoid this problem by changing it to the same value?
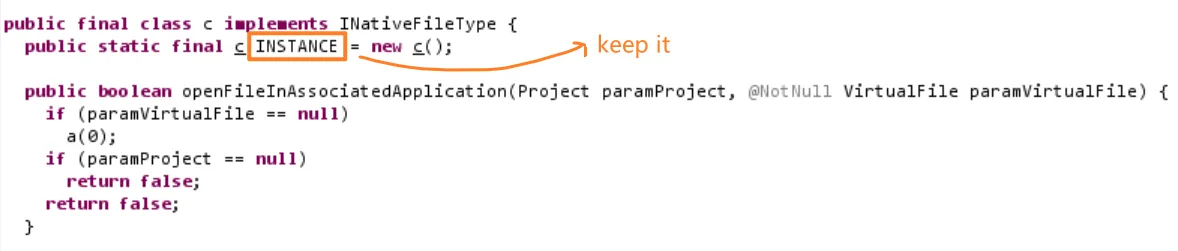
Yes, this is true in principle. However, the obfuscation generates a random variable name each time. That is, the attribute fieldName must have been specified as a certain exact value first, and then the packaging started, and in the class file after packaging, the INSTANCE is not necessarily the value specified above. Therefore, we still need to exclude INSTANCE from the obfuscation rules to avoid this problem.
Local data storage
Section titled “Local data storage”In many cases, there is a need to store some data locally, such as settings data, environment data, etc. In this case, you need to use @State to specify a file to store the data. In this case, you need to use @State to specify the storage file. For example, the
package com.obiscr.template;
import com.intellij.openapi.components.*;import com.intellij.openapi.project.Project;import com.intellij.util.xmlb.XmlSerializerUtil;import org.jetbrains.annotations.NotNull;import org.jetbrains.annotations.Nullable;
@State( name = "com.obiscr.template.MyState", storages = @Storage("my-state/state.xml"))public class MyState implements PersistentStateComponent<MyState> { public String currentVersion = ""; public Boolean enableFeature = true; public String myCustomKey = "";
public static MyState getInstance(@NotNull Project project) { return project.getService(MyState.class); }
@Nullable @Override public MyState getState() { return this; }
@Override public void loadState(@NotNull MyState state) { XmlSerializerUtil.copyBean(state, this); }
}Here a storage file and some properties are defined, it will and a new state.xml file is created in the my-state directory of the project's .idea directory, with the following contents
<?xml version="1.0" encoding="UTF-8"?><project version="4"> <component name="com.obiscr.template.MyState"> <option name="currentVersion" value="v1.0.1" /> <option name="enableFeature" value="false" /> <option name="myCustomKey" value="value" /> </component></project>In the same way, the name attribute in option here corresponds to the three attributes in MyState.java. These attributes should not be obfuscated; if they are, the original data will not be read. For example, if you set:
- currentVersion: v1.0.1
- enableFeature:false
- myCustomKey:value
After obfuscation, assume the following properties in MyState.java:
- currentVersion -> a
- enableFeature -> d
- myCustomKey -> c
The data in state.xml cannot be read at this point. Because there is no option name is: a, d, c data, so the final value read out is the default value defined in MyState.java, once this value has changed, will be in the xml again to add a new attribute. name is the variable name after the obfuscation.
Now the currentVersion has been obfuscated to a, so if the value of currentVersion changes, change it to v1.0.2, then state.xml will look like this
<?xml version="1.0" encoding="UTF-8"?><project version="4"> <component name="com.obiscr.template.MyState"> <option name="currentVersion" value="v1.0.1" /> <option name="enableFeature" value="false" /> <option name="myCustomKey" value="value" /> <!-- Added --> <option name="a" value="v1.0.2" /> </component></project>A <option name="a" value="v1.0.2" /> will be added. So as long as the variable name is not the same after obfuscation, it will keep adding. So here's a way to fix it:
register<proguard.gradle.ProGuardTask>("proguard") { ...
keep(""" class * implements com.intellij.openapi.components.PersistentStateComponent {*;} """.trimIndent() ) ... }This rule ignores all classes that implement PersistentStateComponent.
Summaries
Section titled “Summaries”This article briefly describes how to use ProGuard and obfuscate the IntlliJ plugin and integrate it into a gradle task.
Actually, I prefer to call it a framework. The specific obfuscation rules will need to be customised for your own project. I hope it can help you.
Disclaimer
Section titled “Disclaimer”This is just a demo project for research and study, please use it in your project at your own discretion.
I will not be responsible for any kind of damage caused by using this obfuscation scheme.